Hi Team,
I am an independent security researcher and I have found a bug in your website
The details of it are as follows:-
Description: This report is about a misconfigured Dmarc/SPF record flag, which can be used for malicious purposes as it allows for fake mailing on behalf of respected organizations.
About the Issue:
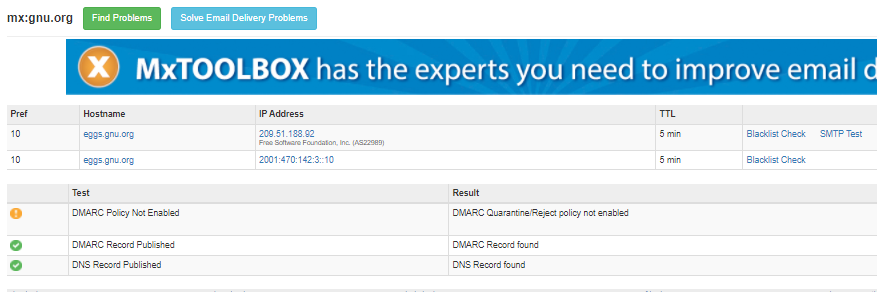
As i have seen the DMARC record for
As u can see that you Weak SPF record, a valid record should be like:-
DMARC Policy Enabled
What's the issue:
An SPF/DMARC record is a type of Domain Name Service (DNS) record that identifies which mail servers are permitted to send an email on behalf of your domain. The purpose of an SPF/DMARC record is to prevent spammers from sending messages on the behalf of your organization.
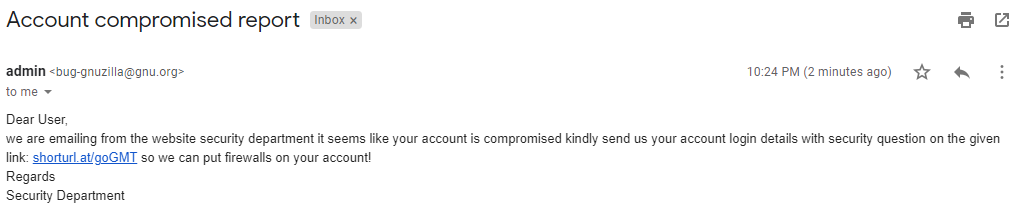
Attack Scenario: An attacker will send phishing mail or anything malicious mail to the victim via mail:
even if the victim is aware of a phishing attack, he will check the origin email which came from your genuine mail id
so he will think that it is genuine mail and get trapped by the attacker.
The attack can be done using any PHP mailer tool like this:-
<?php
$to = "VICTIM@example.com";
$subject = "Password Change";
$txt = "Change your password by visiting here - [VIRUS LINK HERE]l";
$headers = "From:
";mail($to,$subject,$txt,$headers);
?>
U can also check your Dmarc/ SPF record form: MXTOOLBOX
Reference:
https://support.google.com/a/answer/2466580?hl=en
have a look at the GOOGLE article for a better understanding!
I am an independent security researcher and I have found a bug in your website
The details of it are as follows:-
Description: This report is about a misconfigured Dmarc/SPF record flag, which can be used for malicious purposes as it allows for fake mailing on behalf of respected organizations.
About the Issue:
As i have seen the DMARC record for
| DMARC Not Found |
As u can see that you Weak SPF record, a valid record should be like:-
DMARC Policy Enabled
What's the issue:
An SPF/DMARC record is a type of Domain Name Service (DNS) record that identifies which mail servers are permitted to send an email on behalf of your domain. The purpose of an SPF/DMARC record is to prevent spammers from sending messages on the behalf of your organization.
Attack Scenario: An attacker will send phishing mail or anything malicious mail to the victim via mail:
bug-gnuzilla@gnu.org |
bug-gnuzilla@gnu.org |
so he will think that it is genuine mail and get trapped by the attacker.
The attack can be done using any PHP mailer tool like this:-
<?php
$to = "VICTIM@example.com";
$subject = "Password Change";
$txt = "Change your password by visiting here - [VIRUS LINK HERE]l";
$headers = "From:
bug-gnuzilla@gnu.org |
";mail($to,$subject,$txt,$headers);
?>
U can also check your Dmarc/ SPF record form: MXTOOLBOX
Reference:
https://support.google.com/a/answer/2466580?hl=en
have a look at the GOOGLE article for a better understanding!


--- End Message ---